Encrypt confidential information in email communication effectively and securely.
Business emails often contain in-house, personal or other sensitive content that could be intercepted and accessed without authorization if inadequately protected. Ensure all-round encrypted exchange of emails with Email Encryption from Hornetsecurity for reliable, secure email communication.
The Benefits of Cloud-Based Email Encryption

Fully Automated Encryption and Decryption of Your Emails
Outgoing emails are automatically encrypted with one of the common encryption technologies (PGP, S/MIME or TLS), depending on the set policy and availability of the corresponding certificates, without any further user intervention. If the sender’s public key is available, their emails are automatically decrypted and delivered to the recipient.
Encryption of data has become a priority because of compliance requirements as well as enactment of the General Data Protection Regulation. In a business environment, exchange of sensitive files and information takes place primarily via email communication. Cyber criminals rely on the “Man-in-the-Middle” to pick up valuable information here. Encryption of the transmission path is essential to protect this data.

Various Email Encryption Technologies
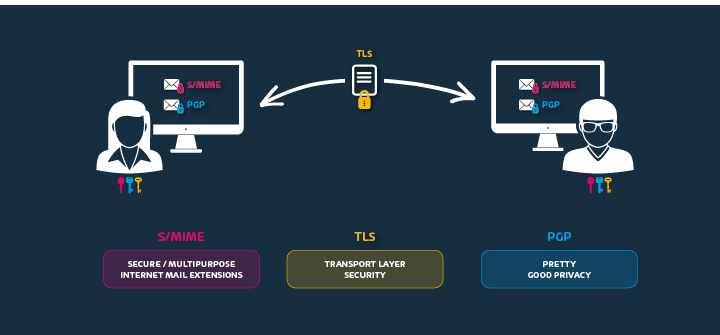
Email Encryption supports all standard encryption technologies, including S/MIME, PGP, and TLS with Perfect Forward Secrecy.
The so-called PKI-based email encryption technologies (S/MIME = Secure / Multipurpose Internet Mail Extensions and PGP = Open Pretty Good Privacy) ensure the confidentiality of transmitted messages between sender and recipient and protect the transported data using cryptographic encryption methods. Hornetsecurity’s encryption service offers this protection directly in the cloud and thus secures the transmission route completely. The TLS protocol is used to ensure confidentiality, authenticity, and integrity when transmitting data over insecure networks.

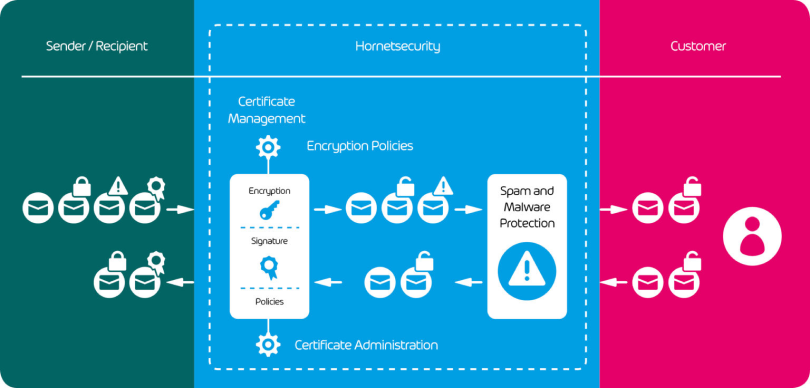
Manage Email Encryption With Minimal Effort
Hornetsecurity provides IT administrators with a variety of ways to easily create and manage email traffic encryption, such as handling user certificates or customizing encryption policies.
Encryption settings can be made either globally or individually for specific users, groups, or domains.
Hornetsecurity Email Encryption Fatures Overview
Confidential communication via Websafe
Even if the communication partner cannot receive encrypted emails, the encryption and confidentiality of email communication with those individuals is still guaranteed.
Automatic digital signing & encryption of outgoing emails via S/MIME and PGP
Secure emails against unauthorized modification or access by third parties during transmission over public networks.
Automatic certificate management & key storage
Hornetsecurity handles procurement and installation of the certificates required. These are stored in a central certificate store.
Individual setup and definition of encryption policies
Clear rules for encryption of email traffic can be set for the entire company. The control panel is used to define which encryption types are used to establish contact with communication partners: TLS, S/MIME or PGP. This is possible either as a package or individually for specific users, groups or domains. In addition, you can define how to proceed if the key of a recipient is not available.
False Facts Identification
Hornetsecurity uses 2048-bit coded certificates, one of the largest and most reliable certificate authorities (CA). When encrypting with S/MIME and PGP, each user receives their own certificate. With PGP it is also possible to use a single certificate for an entire domain. Alternatively, certificates supplied by the customer can also be imported and used.
Confidential communication via Websafe
Even if the communication partner cannot receive encrypted emails, the encryption and confidentiality of email communication with those individuals is still guaranteed.
Integration of the Email Encryption into the Email Management System
Email Encryption from Hornetsecurity handles all aspects of certificate management. Encryption, decryption and signing take place automatically and transparently for incoming and outgoing emails. In order to guarantee the functionality and efficiency of Email Encryption, integration of spam and malware protection is required.